System Fundamentals
1.1 Systems in organisations (10 hours)
by M Brooke
Planning and system installation
1.1.1 Identify the context for which a new system is planned
Data gathering
In the initial planning stages there will be a process of investigation into the current system, this will involve the collection of data in a variety of ways (observation, interview, questionnaire, document collection)
Each of these has its advantages and disadvantages:
Investigation | Advantages | Disadvantages |
Interview | Detailed information with key people. Two way and face to face. | It is very time consuming. |
Questionnaire | Can reach large audiences quickly and the data can be used to create extensive analysis. It is quick. | Questionnaire may not be well designed and people may not answer it or may answer it incompletely or incorrectly. |
Document Collection | Good quality objective data about the inputs, outputs, and processing taking place within the system. | Documentation may be limited or inaccurate |
Observation | Can gain first hand unbiased information. | Things and people change when they are being observed |
Requirements specification
Following that there will be an analysis of the system in terms of how it works. The inputs process and outputs of the system will be identified and any problems associated with the current system
This allows the analyst to produce the requirements for the new system. Leading the the creation of the requirements specification. This is a tightly controlled process and set out in the IEEE standard [1].
The requirements specification is a key document in a traditional life cycle as it drive all subsequent work. It is also the basis for projects success and is often known as the success criteria.
This stage of the project clearly identifies the context in which the new system is planned and will take into account considerations and justifications of the technologies for the new system and any other requirements in terms of success criteria.
Issues
There may be several issues relating to people using new systems. Clients and managers of the new system may need retraining and there will be a period of readjustment to anew system In it's more extreme case this could lead to unemployment.
The context of the system in terms of existing technologies needs consideration. Will the current hardware and software infrastructure be able to deal with the new system in terms of network bandwidth, storage processing power or operating systems.
1.1.2 Describe the need for change management
Change management is the movement towards a future desired state. This may affect a variety of people or organisations depending on the change required. This is managed with a structured approach. Change management may occur on an organisational level or may be related to individual systems. Change management may occur in many places such as:
- Hardware
- Communications equipment and software
- System software
- All documentation and procedures associated with the running, support and maintenance of live systems
Without effective change management there may be serious issues in systems in as much as they may simply stop functioning or may contain bugs or errors that become difficult and costly to fix if the change has not been well documented or thought through.
In order to be effective the change must fulfill a number of criteria such as
- Approval by management
- Implemented with minimal and accepted risk to existing infrastructures
- Provides an improvement in terms of functionality or stability
ISO 20000 defines the objective of change management (part 1, 9.2) as:
“To ensure all changes are assessed, approved, implemented and reviewed in a controlled manner.”
The adherence to and certification in the ISO process can be managed by third parties such as:
http://www.isoiec20000certification.com/
1.1.3 Outline compatibility issues resulting from situations including legacy systems or business mergers
Legacy systems
“A computer system or application program which continues to be used because of the cost of replacing or redesigning it and often despite its poor competitiveness and compatibility with modern equivalents. The implication is that the system is large, monolithic and difficult to modify.
If legacy software only runs on antiquated hardware the cost of maintaining this may eventually outweigh the cost of replacing both the software and hardware unless some form of emulation or backward compatibility allows the software to run on new hardware.” [1]
Business mergers
A business merger is the joining of two businesses. This may create several problems, The systems used by the companies may be very different. This can result in time and money being spent converting one system to another. It may be that two systems will continue to run independently which may cause problems in terms of data redundancy. If systems are to be replaced then this will have a cost in terms of purchasing new hardware and software and retraining staff to use the new system.
1.1.4 Compare the implementation of systems using a client’s hardware with hosting systems remotely
When deciding whether to use local hardware or utilise the cloud there are several considerations that must be made. There are four main models of computing that can be offered in the cloud.
Infrastructure as a Service (IaaS)
Platform as a Service (PaaS)
Software as a Service (SaaS)
Network as a Service (Naas)
Each of these will have their pros and cons in terms of hosting locally or in the cloud. Below are some general evaluations of these.
Cloud computing
Advantages | Disadvantages |
Convenience Security Backups Collaboration Environmentally Friendly | Security Service outage Storage limits Slow speeds Limited features |
Local computing
Advantages | Disadvantages |
Security Backups can be controlled Legacy software Software control Feature control | Cost of hardware Technical support Lack of collaboration |
1.1.5 Evaluate alternative installation processes
Direct
The old system is stopped and the new system is started.
Advantages | Disadvantages |
Minimal time and effort. New system is available immediately. | If the new system fails there is no backup. |
Parallel
the new system is started but the old system is kept running alongside. Data is input into both systems.
Advantages | Disadvantages |
If new system fails the old system runs as a backup. The outputs form the two systems can be compared to see if the new one is running correctly. | Running two systems is costly in terms of time and money. |
Pilot
The new system is piloted (trialled) in a small part of the business. One it is running correctly then the new system is implemented across the organisation.
Advantages | Disadvantages |
All features can be fully trialled. If the new system fails only a small part of the organisation suffers. Staff who were part of the pilot study can train other staff. | For the section that is piloting if the system fails there is no backup. |
Phased
the new system is introduced in phases as parts of the old system are gradually replaced with the new system.
Advantages | Disadvantages |
Allows people to get used to the new system. Training can be done in stages. | If the new part of the system fails there is no backup for that area. |
1.1.6 Discuss problems that may arise as a part of data migration
Making sure that a set of success criteria are clear before the process is on eof the most important aspects of the migration and this needs to be done with the main users of the system. It is often handled by the technical team but they are not going to be the future users and so consultation with the appropriate stakeholders is essential.
There may be poor quality data in legacy systems and this will need to be checked in terms of its integrity and also in terms of how it needs to be modified for use in an updated system.
Testing and validation needs to be taking place at all stages throughout the migration and this needs to be well planned before the migration. Data may be in diffenrent formats in the new system and this may be due to such facotrs as different currencies, different date formats or different character sets. This will need to be identified and resolved before the data is input into the new system. Backups must be taken throughout the process in case data is corrupted or migration is incomplete.
1.1.7 Suggest various types of testing
Testing is conducted at several stages of the software development. The testing at each stage will be dependant on the stage and may be simply debugging code or user acceptance testing or even beta testing when the initial design has been completed but is not yet on general release.
Detailed test plans will be created and a typical test would contain:
- Details of what is being tested
- The test data to use
- What is expected to happen when the test is performed
When choosing the data we need to consider why we are testing: to see if the system works well and that the system does not break. In order to do this we can discern three types of test data
Normal
This is data that would be expected to be entered in the system. The system should accept it and process it.
Extreme
Extreme values are still normal but are at the edges of acceptable and are used to see that the system responds correctly to all normal data.
Abnormal
This is data that should not be accepted. The system should be able to handle this data without crashing or breaking. Validation checks and the handling of exceptions are often used to ensure this data is handled well.
User focus
1.1.8 Describe the importance of user documentation
User documentation describes how the product is used for a user of the system. It will describe each element of the system and assists the user. It is important that this document is not confusing and is written in a clear language. It must also be as up to date as possible. There are three broad approaches that this documentation can take:
- Tutorial
- Thematic
- List Reference
Tutorials give users practical exercises to do and guided through a task. A thematic element will often be chapter based and go systematically through each feature. Lists or references are useful for technical users who want quick reference to features. Documentation is best when a mix of all three are present.
1.1.9 Evaluate Different Methods of providing user documentation
Manuals
These can be provided online or offline. an example of an online manual can be seen for the wave editor Audacity at http://manual.audacityteam.org/o/. This is in the form of a webpage and lets the user browse chapters of the manual and has tutorials. One of the bonuses of online manuals is the potential use of multimedia elements which cannot be placed in a printed manual.
Manuals can also be provided online as a pdf such as the manual for Ableton Live at http://downloads.ableton.com/manuals/80/ableton_live_8_manual_en.pdf. These have the advantage of being able to be printed. The advantage of the printed version is that it can be read and referred to away from the computer or an internet connection.
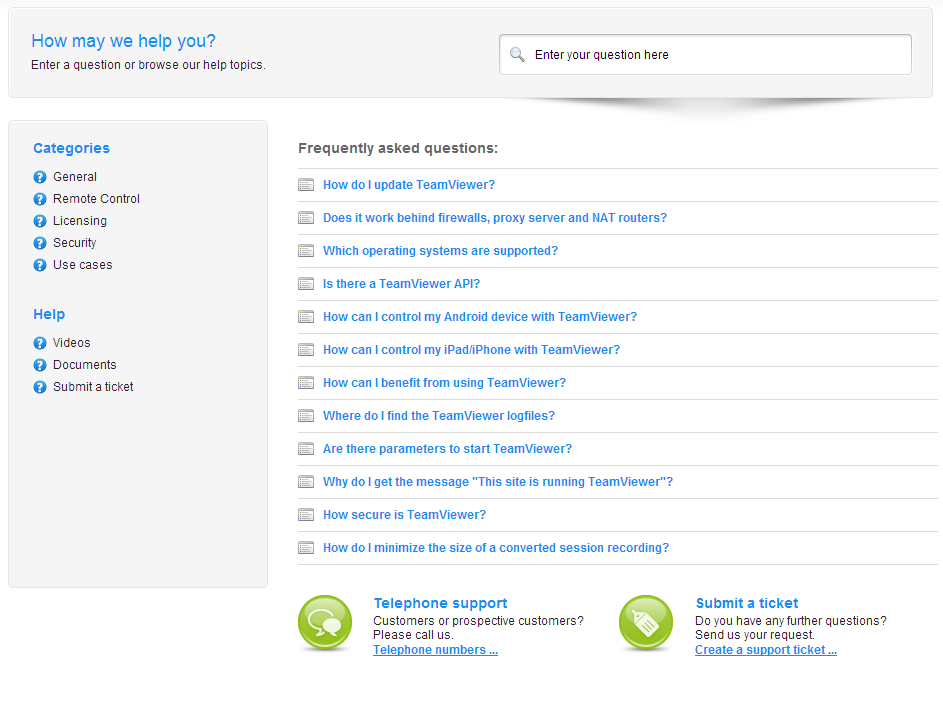
FAQ
Frequently asked questions can also be provided both online and offline to give users answers to a common set of problems that users of the system experience. They generally relate to usability issues. The screenshot below gives and example[2]:
Online portals
Online support is provided in many ways depending on the product or service that is being documented. Online portals can provide manuals in the form of web pages or print versions in Portable Document Format (PDF). The can also provide FAQ pages as described above. The advantage of online portals is that they are more likely to provide up to date information. Companies will also often provide a range of support services from an online site.
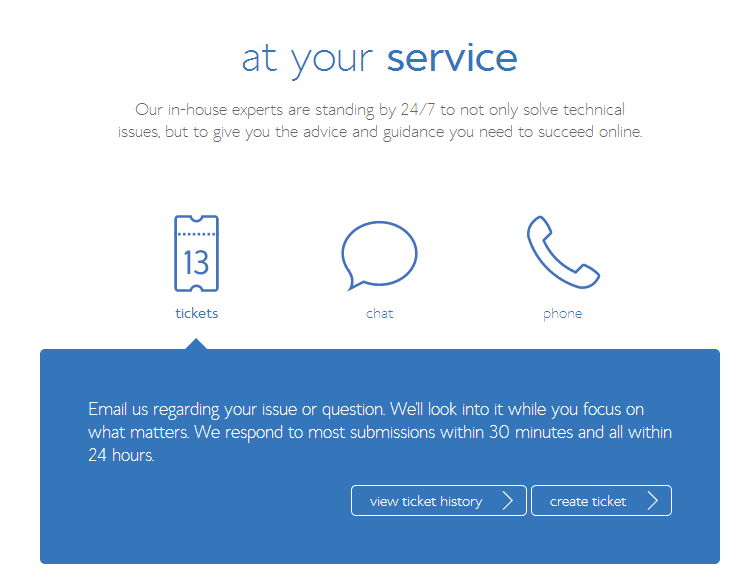
email support
For example online support can be provided by a ticket system via an email address where you contact their support team and your problems are resolved by technicians via a ticketing system. an example of this is Zendesk. This is an asynchronous type of support as you have to wait for and responses to question but you are more easily able to track issues with ticket numbers and support ticket threads.
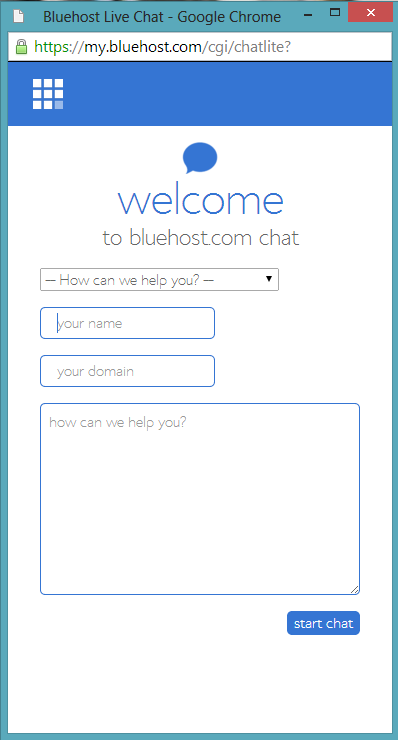
Live chat sessions
Online support can also be through a live chat or video session whereby you can get real-time support from a technician. This support gives a feeling of being supported by a real person and this is prefered by many people. It is also real time so can be useful for issues that need resolving quickly.
This real-time support may also be a video call.
Remote desktop connections
Support may also be offered by a remote desktop connection where a technician will connect to and be able to control your computer to see first hand what the problem is and resolve it for you. This solution is ideal if you want your problem solving quickly and also is very useful if the user is not very experienced. there are obviously some security issues here as you are granting an unknown (albeit trusted) third party access to your computer. Products such as Teamviewer offer this type of service.
Embedded Assistance
Many systems now come with user documentation such as tool tips and tool tips and dynamic page content within the system itself.
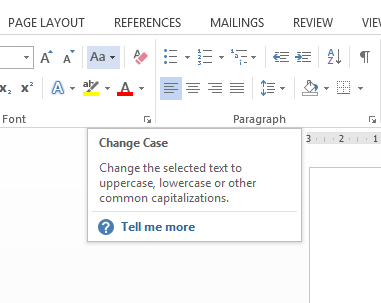
One example is when you mouse-over an icon a small box appears with help information:
Programs will often have inbuilt help systems such as this example in Microsoft Word:
1.1.10 Evaluate different methods of delivering user training
User training can be delivered in a number of way. This will be handled differently depending on a variety of factors such as the size of the business, and the training budget. Other factors such as the type of system will influence the most appropriate method.
Self Instruction
Advantages
Self instruction will allow the student to learn whenever it is required. Manuals or other resources such as videos or exercises can be provided and used whenever the user has the need to find out a particular skill. This means the learning is done exactly when it is needed and there is no additional unnecessary time wasted on unneeded skills. There can be a cost saving as the there is no course to pay for or place to rent or instructor to pay and there is no time lost in training sessions.
Disadvantages
The effectiveness is based upon several issues such as the motivation of the user and their ability to learn on their own. If the materials are not well prepared or suited to the users learning styles or level of understanding there may be several issues.
Formal classes
Advantages
Having a formal classroom to conduct training allows an open exchange of ideas in real time. This can happen between the instructor and the students and there are no barriers to communication or delay as may be experienced in an online situation. A formal classroom can tend to focus the learning and gives a more social element to the process which many feel is essential. The classroom can provide a “real time” space to ask questions and resolve issues.
Disadvantages
A classroom situation may disadvantage more shy members of the group and can be dominated by more vocal and demanding members of the group. It can often be hard for instructors to isolate or teach those who are having difficulty as there may not be the time to support them or the need may not even be noticed in a large group.
Remote/online training
Advantages
Training can take place anywhere at any time and this allows training to be delivered globally across large distances and across many time zones. The fact the resources are available at anytime means that people have flexibility in how they fit the learning in around their own schedules. Also this allows training resources to be revisited or revised easily.
There is a strong element of synergy in online training as the interaction and reflection of a large number of people in an asynchronous dialogue creates an improved training effect that is greater than the sum of the separate individual effects.
There is a level playing field and discriminating effects such as age, gender, appearance, disability and race are reduced or even in some cases absent. it is also easier to include distinguished experts or train people from other companies.
Online training is also student centred due to reflection and dialogue with other students from the initial resources.
Disadvantages
In order for online training to be feasible there must be an equity in the access or provision of the required technology. there may be economic or logistical reasons for this not being the case. This may be as simple as the provision of computers or the access to a reliable internet connection. Problems also occur in the differences in computer literacy. If these skills are not present then the training will not be successful. The course itself must be user friendly and reliable if it is to succeed.
Good trainers in the “real world” do not necessarily make good instructors in the online environment and they will need to have a high level and understanding of the requirements and success criteria of running an online environment.
There are some things that cannot be taught online as the limitations are too great and a face to face or hands on approach is necessary.
System backup
1.1.11-1.1.13 Identify a range of causes of data loss. Outline the consequences of data loss in a specified situation. Describe a range of methods that can be used to prevent data loss
Accidental deletion
This is a very common cause of data loss and depending on what files are deleted can lead to serious issues other than just the loss of a word document. Deleting system files may be an example of this. There are a large number of file recovery softwares available and these can be very effective if the user is prepared and acts quickly. Filesalvage is an example of this type of software for Macs.[3]
Computer Viruses
There are many viruses and malware that will delete files once the system has been infected and is is essential that a good antivirus solution is put in place. Updates must be done frequently along with regular scans. There are several reputable suppliers of antivirus solutions such as Symantec. [4]
Physical damage
Hard drives are sensitive machines and can be easily damaged if they are not handled with care.Ensuring that hardware is treated with care and kept at the correct temperatures will help minimise this.
Continued use after signs of failure
Strange noises, system crashes or hangs and other signs of imminent problems are often ignored against the better judgement of the user and this can have consequences if it leads to a failure. Self-monitoring, analysis and reporting technology[5] (SMART) is a monitoring system for HDDs and SSDs that detects and reports on reliability and indicators of failure. These are not failsafe systems but may help to anticipate problems or force a safe shutdown or backup before failure.
Power failure
This is a common cause of data loss. This can lead to loss of unsaved files or even corruption of files. This can be minimised by the use of an uninterruptable power supply[6] which this provides near instantaneous protection from power interruptions by means of power stored in batteries. Depending on the size of the UPS this will allow the system to shut down safetly until normal power is returned or to remain on until power returns.
Firmware corruption
The firmware on a hard drive controls how it operates and reads and writes to the disk. If the firmware becomes damaged the OS cannot recognise the disk. It is difficult to guard against this but it can be resolved through the use of backups or even swapping out the logic boards within the drive.
Natural disasters
lightning strikes, power surges, flood, fire, earthquakes and other “acts of god” can cause damage to hardware. Ways to minimise these are to have good quality surge protectors to guard against spikes in power supply[7]. Backing up copies of your data offsite at another location or with a cloud backup solution will help to minimise data loss.
Software deployment
1.1.14 Describe strategies for managing releases and updates
Release management
Release strategies will vary from organisation to organisation. Some of the stages software may go through in its release cycle are as follows:
Pre-Alpha
An interim product release that does not contain all the features required but may demonstrate certain elements that have been built.
Alpha
An internal release delivered to the testing group. It will contain a preliminary build that is partially complete.
Beta
First product release for outside testing. Contains all features but has known issues and bugs.
Release candidate
All features are completed and there will be no additional new code but there may still be unwanted bugs to be fixed. This stage is often called code complete.
General availability
Stable release relatively bug free exceeds expectations of client.
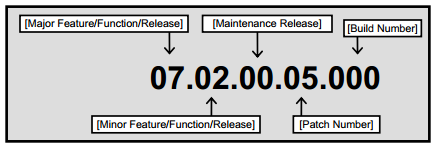
Release numbering
This many appear to be a trivial matter but is very important in identifying and managing release strategy. The following is an example of IBMs numbering system:
Now test yourself
https://quizlet.com/121432976/test/embed
[1] "Legacy system | Define Legacy system at Dictionary.com." 2008. 8 Apr. 2014 <http://dictionary.reference.com/browse/legacy+system>
[2] "Suporte TeamViewer – Ajuda sobre licenças e questões técnicas." 2012. 4 Apr. 2014 <http://www.teamviewer.com/Pt/help/index.aspx>
[3] "FileSalvage - SubRosaSoft.com Inc." 2012. 3 Apr. 2014 <http://subrosasoft.com/software/filesalvage>
[4] "Symantec: Endpoint, Cloud, Mobile & Virtual Security Solutions." 2003. 3 Apr. 2014 <https://www.symantec.com/>
[5] "S.M.A.R.T. - Wikipedia, the free encyclopedia." 2005. 3 Apr. 2014 <http://en.wikipedia.org/wiki/S.M.A.R.T.>
[6] "Uninterruptible power supply - Wikipedia, the free encyclopedia." 2003. 3 Apr. 2014 <http://en.wikipedia.org/wiki/Uninterruptible_power_supply>
[7] "Surge protector - Wikipedia, the free encyclopedia." 2004. 3 Apr. 2014 <http://en.wikipedia.org/wiki/Surge_protector>